|
Background
Microsoft showed Active Directory to the world when Windows 2000 was launched. Active Directory mainly verifies the logged-in users, applies group strategy to users and computers and helps them find the printers they need. Later, in Microsoft's important version of Windows Server 2003, Active Directory was greatly improved. Active Directory is no longer a specific technology, but a brand that represents a range of Windows identity and access control services.
Because of this, Active Directory is fully supported and deployed by many large and medium-sized enterprise users. With the development of these large and medium-sized enterprises in the actual application deployment process, they are facing more and more severe challenges in the use of identity and access control service management:
- There are password sharing, borrowing and embezzlement among employees
- Staff passwords are often easy to forget
- The pressure of administrator's operation and maintenance is increasing day by day
Therefore, for the requirements of AD domain control management proposed by enterprises, we customize a set of AD domain two-factor authentication (2FA) management solution based on fingerprint identification for enterprises.
Discription
A. Programme Characteristics
| Characteristics |
Discription |
| Safe |
Platform and network fingerprint authentication technology is different from traditional client authentication mode, safe and reliable, and may achieve multi-factor authentication according to security needs. |
| Roles Independence |
According to the principle of "separation of three Roles" in security management of secret-related systems, the system functions are designed to make the system more suitable for the needs of practical management and make the security strategy more robust. |
| Distributed Network Deployment Architecture |
AD Server, Fingerprint Identification Server, WEB server are deployed in different servers to reduce the possibility of server system instability caused by excessive close integration of the system. The security backup strategy is adopted to ensure the security of fingerprint storage. Web Service technology is used to penetrate the firewall without obstacles. |
| Easy to use |
AD domain user identity management mode based on B/S architecture of JAVA technology can centralize the management of domain users anytime, anywhere. |
| Support many devices |
It can support dozens of international mainstream fingerprint acquisition devices, realize cross-comparison application, unify standard software and hardware application interface, and meet the secondary integration of B/S C/S architecture application system. |
| Preventing Fingerprint Database Leakage |
Key used to manage fingerprint databases is specially encrypted. Only system administrators know that fingerprint feature templates are invalid even if the database is compromised without Key decryption. |
| Storage security |
The system does not save the fingerprint eigenvalue template, but saves the key template encrypted by fingerprint eigenvalue processing. The user activates the encryption key through fingerprint identification, and no longer controls the core authority of the encryption system by any third party. Based on the randomness of fingerprint reading, the generated key is also on-line and effective at one time, which significantly improves the security level of the key and achieves the secure fingerprint. Identity authentication |
| Diversity of Identity Authentication |
Users can set up single-finger/multi-finger/multi-person authentication according to different classifications to ensure the security of the classified information. |
| Dynamic password policy |
Password Dynamic Update, Military Password Rules |
B. Design
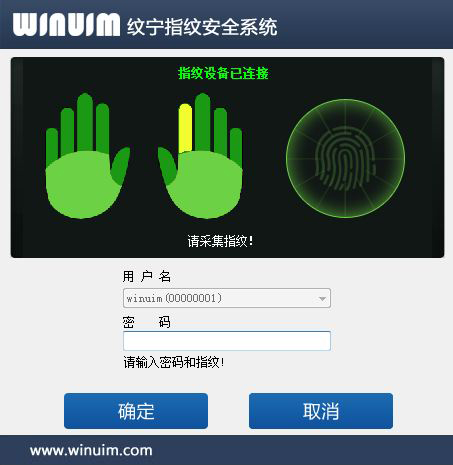
Fingerprint verification has high security, fast identification speed and high recognition accuracy; neither unregistered nor illegal fingerprints can pass verification, that is, fingerprint login operating system can not be realized; cross-regional secure login to Windows client, real-time query of log records can be realized; at the same time, it is compatible with offline fingerprint login, and is not affected by network conditions.
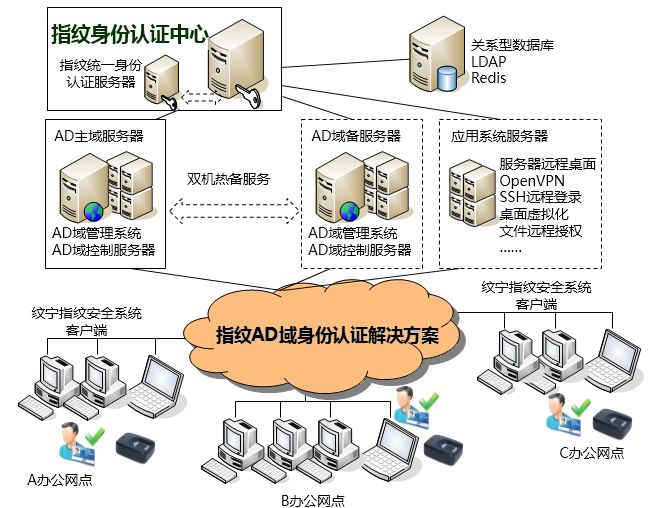
Chart 1: Schematic diagram of fingerprint AD domain management system
Chart 2: Windows Client-side Two-Factor Authentication (2FA) UI
The fingerprint AD domain management identity authentication solution consists of the following parts:
(1) Windows AD Domain Control Server
(2) fingerprint AD domain management system
(3) Unified fingerprint identity authentication system
(4) Windows fingerprint security system client software
(5) Fingerprint acquisition terminal
OS supported:
(1) Windows Server----Windows2003/Windows2003 R2/Windows2008/Windows2008 R2/Windwos2012 32/64bit
(2) Windows Client----WindowsXP/WindowsVista/Windows7/Windows8/Win10 32/64bit
C. Devices for chosen
|
Model |
Desc. |
|
WMR06 Fingerprint Scanner
 |
- n vivo detection technology, the imaging quality is excellent and the performance is superior.
- Small and portable
- Pressure acquisition
- Suitable for personal and enterprise users
|
|
WMR08 Fingerprint Scanner
 |
- Suitable for public places, generous and dignified Compression acquisition
- with fast acquisition speed and 360 degree rotation acquisition
- Fingerprint imaging quality is excellent, image accuracy is high, and performance is superior.
|
|
WMFV11 Vein Scanner
 |
- Identification of finger vein in vivo and elimination
- Compression acquisition and infrared light-induced venography
- The biometric recognition rate was 100%
- Finger vein imaging has excellent quality, high image accuracy and superior performance.
|
D. Value
- Strict control of identity rights, based on fingerprint authentication mechanism, to achieve accurate control of access rights and authorization, protect the safe use of data
- Simplify the login authentication process, save the trouble of keyboard password input, optimize user authentication experience
- Reduce IT Maintenance Cost, Remove Password Reset Work, Liberate IT Maintenance Productivity
- Enhance the effectiveness of network internal control, based on fingerprint authentication, ensure that the deployment of identity and privilege is fully consistent with the actual security strategy, and solve the security management problems.
- Trusted Audit of Mass User Identity, System Log-in and Privilege Access in Unified Centralized Management Domain System
- Web-based domain management, AD domain and fingerprint server can realize synchronous information transmission and coordinated information management
- Support server remote desktop fingerprint login, desktop virtualization fingerprint login, VPN fingerprint login, file fingerprint authorization encryption and decryption extension application
- Open Access Design to Support Verification of Different Terminal Devices
E. 2FA Experience
Please write an email to us: services@winuim.com ,and we will arrange technical engineers to build a trial environment for your experience.
| |